
IoT Security
Strategies for Protecting IoT from Cyber Attacks

Using Internet of Things (IoT) devices across enterprises, healthcare and industrial applications delivers productivity benefits, but it also exposes you to new cyber-threats.
Overview
Protecting IoT Devices
With 63% of enterprises, 92% of industrial organizations and 82% of health care organizations using IoT, almost every company is exposed to cyber-attacks. IoT devices make life easier for businesses. Unfortunately, connecting IoT devices to the network extends the attack surface which provides more entry points for hackers.
- Identifying IoT security risks across IT/OT networks
- Creating policies to quickly secure IoT devices
- Preventing both network-based and device-level attacks
Key Benefits

IoT Discovery & Risk Analysis
Uncover all the unmanaged and IoT devices in your network and their risks

Zero-Trust Segmentation
Enforce zero trust policies to prevent unauthorised access and lateral movement

IoT Threat Prevention
Block known and zero-day attacks with virtual patching and real time IoT threat intelligence
Check Point IoT
Check Point IoT Protect prevents IoT cyber attacks, adapting protections to any IoT or OT device across smart-office, smart-building, medical and industrial environments.
Delivering zero-trust policy tailored per device, Check Point IoT Protect uses:
- Real time threat intelligence
- 60 innovative security services
- On-device runtime protection to deliver a complete, end-to-end prevention-first strategy for an ever-evolving cyberphysical world
Tailored for Any IoT Environment

Enterprise

Healthcare

Industrial

Manufacturing
IoT Risk Analysis and Zero-Trust Segmentation
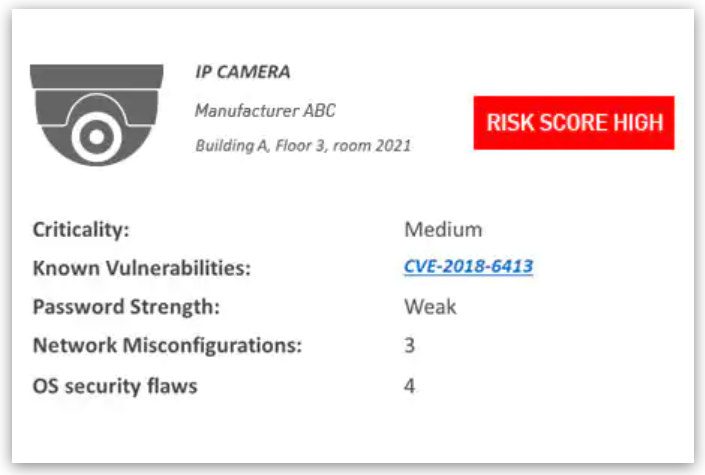
Assess all the risks associated with your devices in any given moment
Real-time risk analysis based on IoT networks discovery, firmware risk assessment and threat intelligence.
From a single console, view all your IoT devices classified based on their risk level. You can even drill down for a risk analysis per device.
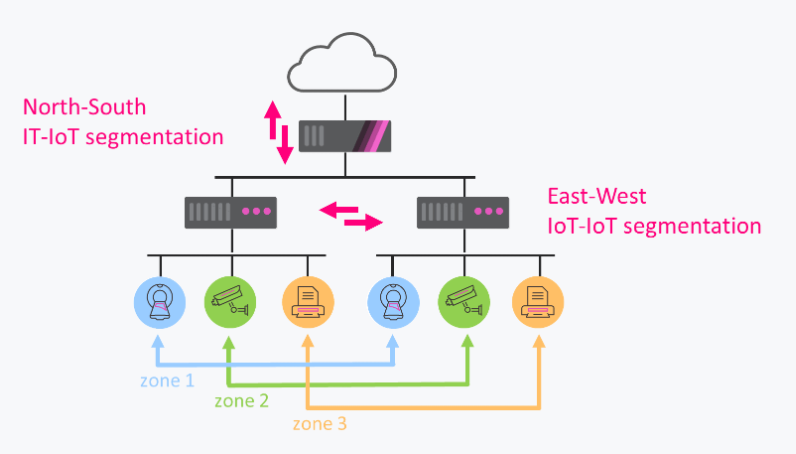
Enforce zero trust to minimize your IoT attack surface
Zero Trust in Source: Prevent unauthorised access and malicious internet from reaching IoT devices
Zero Trust in Destination: Prevent infected devices from moving laterally and accessing malicious sites
Auto-generated policies: Minimize your risk exposure and save months of manual policy configurations
See and control over 1,500 IoT/OT protocols & commands
IoT Security
The IoT Security Gap
IoT devices are inherently vulnerable and poorly protected, which makes them attractive targets. Cybercriminals are continually looking for new ways to breach devices, or use them to infect other critical systems. It is time to take action and keep every device secure.
Prevent Cyber Attacks on Networks and IoT Devices
Don't leave your IoT Security to chance. Get the visibility you need and the security you deserve with Check Point IoT Protect.

