Check Point IPS Software Blade
Delivers complete and proactive intrusion prevention

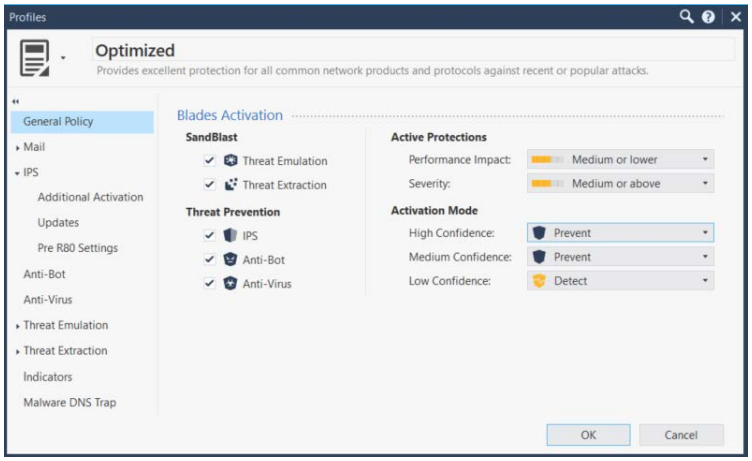
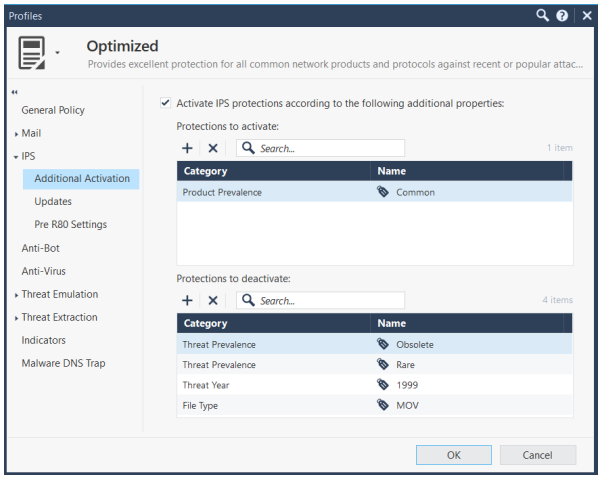
Intrusion Prevention Systems detect or prevent attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking threat. Check Point IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago, or a few minutes ago, your organization is protected.
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
Click here to jump to more pricing!
Please Note: All prices displayed are Ex-VAT. 20% VAT is added during the checkout process.
Overview:
Intrusion Prevention Systems detect or prevent attempts to exploit weaknesses in vulnerable systems or applications, protecting you in the race to exploit the latest breaking vulnerability. Check Point Intrusion Prevention System (IPS) provides complete, integrated, next generation firewall intrusion prevention capabilities at multi-gigabit speeds with high security effectiveness and a low false positive rate. IPS protections in our Next Generation Firewall are updated automatically. Whether the vulnerability was released years ago or today, your organization is protected.
Our defense in depth approach combines signatures, protocol validation, anomaly detection, behavioral analysis, and other methods to provide the highest levels of network IPS protection. Check Point IPS provides complete threat coverage for vulnerabilities in clients, servers, operating systems and widely available applications such as PDF readers and browsers that are the preferred targets of threat actors.

Secure
Check Point IPS delivers thousands of signature and behavioral preemptive protections
Efficient
Our acceleration technologies let you safely enable IPS. A low false positive rate saves your staff valuable time
Unified
Enable IPS on any Check Point security gateway reducing Total Cost of Ownership
Online attacks and malware have been evolving, using sophisticated and even evasive attack methods. Check Point addresses the changing threat landscape while meeting several key operational requirements for Intrusion Prevention Systems. Check Point IPS protections include checks for protocol and behavioral anomalies which means we detect vulnerabilities in well-known protocols such as HTTP, SMTP, POP, and IMAP before an exploit is found.
Check Point IPS protects you with:
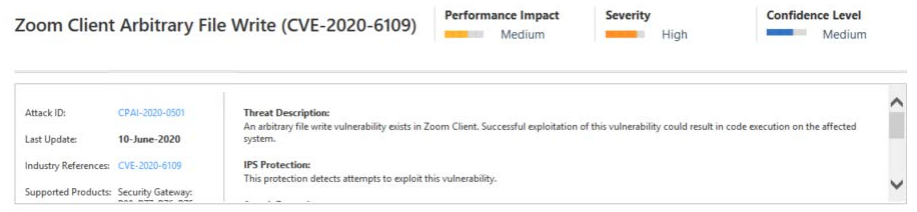
- Detection and prevention of specific known exploits, for example protection from specific CVEs
- Detection and prevention of DNS tunneling attempts indicating data leakage or evasion
- Detection and prevention of generic attack types without any pre-defined signatures
- Detection and prevention of protocol misuse which may indicate malicious activity
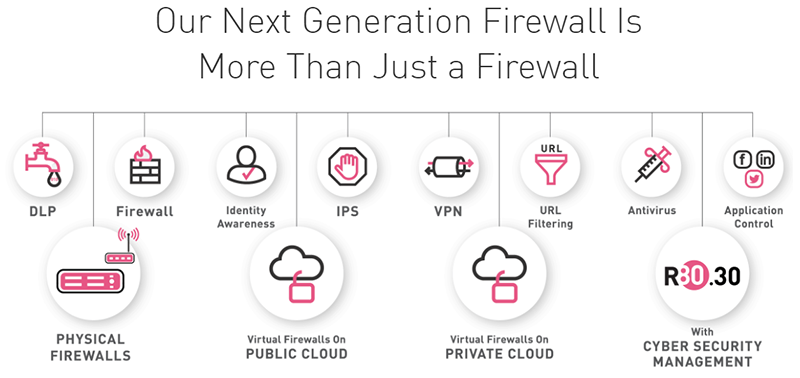
Pricing Notes:
- All prices displayed are Ex-VAT. 20% VAT is added during the checkout process.
- Pricing and product availability subject to change without notice.
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote
*The purchase of a Security Gateway container is required per user
Our Price: Request a Quote